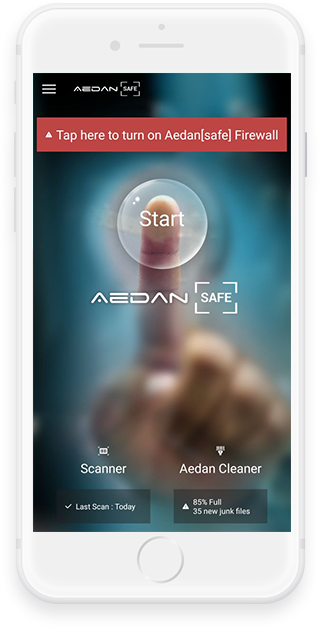

When users install mobile applications to their devices, the application requests specific permissions and access to various sensitive information such as contact lists, local storage, device cameras, network activities and your microphone.
If and when an attacker hijacks one application with access to any of these permissions, the attacker may control the user device. Text messages, screen capture, and payment information can be easily compromised without proper security.
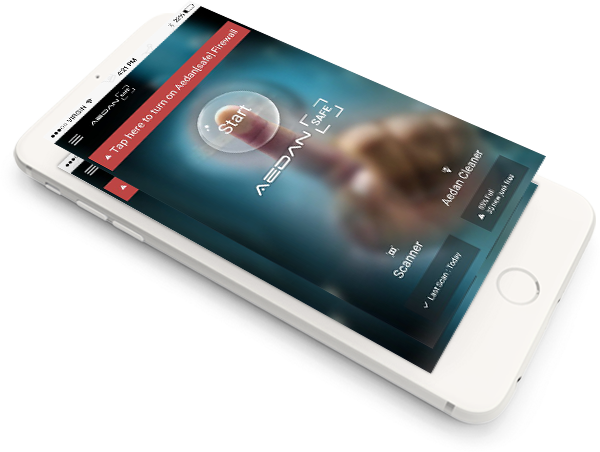
Aedan uses several preemptive security Solutions created by Hackers and Scientist to protect your data, defend your privacy and optimize the performance of the user device.
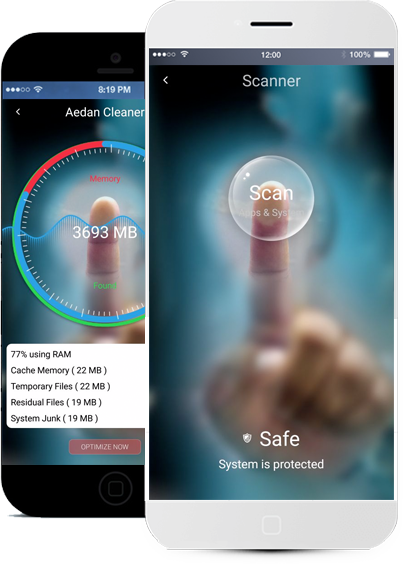
Definition of Artificial intelligence: Allen Turing proposed that a computer can be said to possess artificial intelligence if it can mimic human responses under specific conditions.
Aedan's Artificial Intelligence engine automates what a professional user would do to keep its device secure and performance in optimum efficiency.
Need to report an attack or security breach? Let us know